Detailed explanation of data structure: from array to tree, and then to hash table
This article discusses several common data structures in depth, including arrays, linked lists, binary search trees (BSTs) and hash tables, and explains their organization in memory and their advantages and disadvantages.
Information structure and abstract data structure
Information structure refers to the way information is organized in memory, while abstract data structures are our conceptual understanding of these structures. Understanding abstract data structures helps us better implement various data structures in practice.
Stack and Queue
Queues are an abstract data structure that follows the FIFO (first in, first out) principle, similar to waiting in line. Its main operations include enqueuing (adding elements to the tail of the queue) and dequeuing (removing the head elements of the queue).
The stack follows the LIFO (Last In First Out) principle, just like stacking a plate. Its operations include pushing (adding elements to the top of the stack) and popping (removing top elements of the stack).
Array
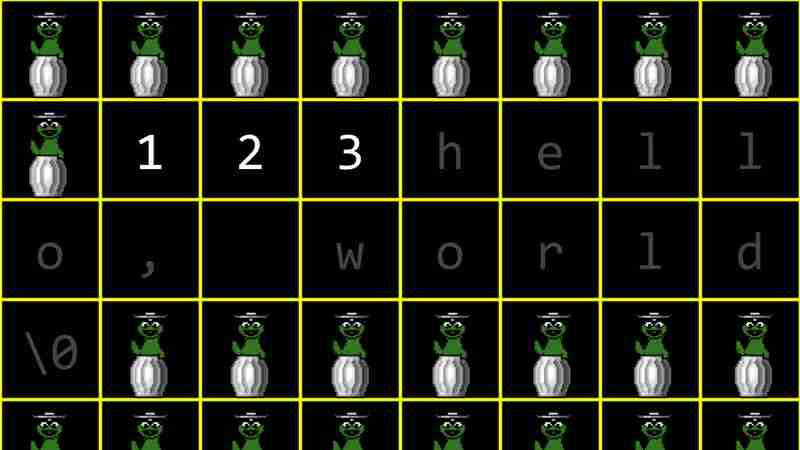
An array is a structure that continuously stores data in memory. As shown in the figure below, arrays occupy continuous storage space in memory.
Other programs, functions, and variables may exist in memory, as well as redundant data that has been used before. If you need to add new elements to the array, you need to reallocate memory and copy the entire array, which can be inefficient.
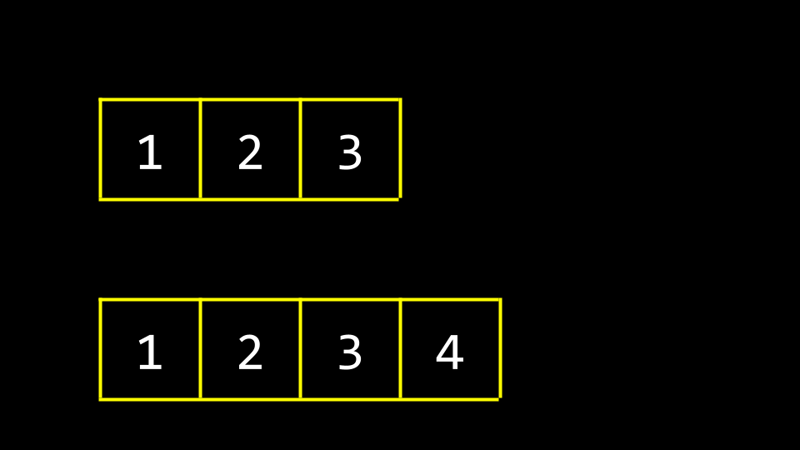
Although pre-allocating too much memory can reduce copy operations, it will waste system resources. Therefore, it is crucial to allocate memory according to actual needs.
Link List
Linked lists are powerful data structures that allow concatenation of values ??located in different memory regions into a list and support dynamic expansion or reduction.
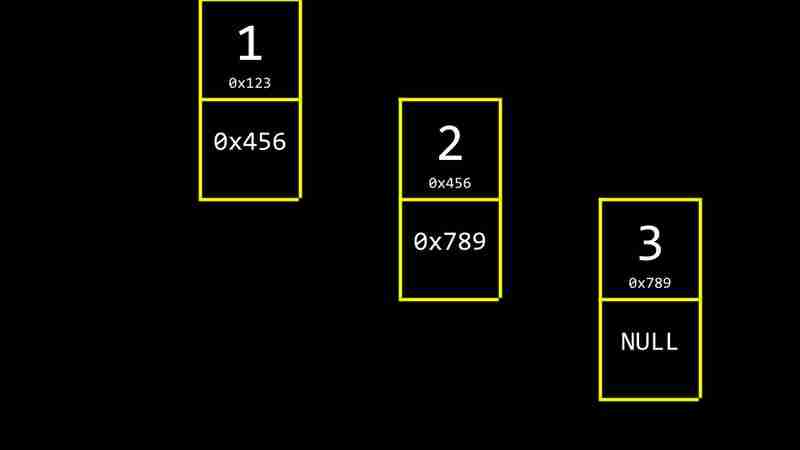
Each CS- Week 5 contains two values: the data value and a pointer to the next CS- Week 5. The pointer value of the last CS- Week 5 is NULL, indicating the end of the linked list.
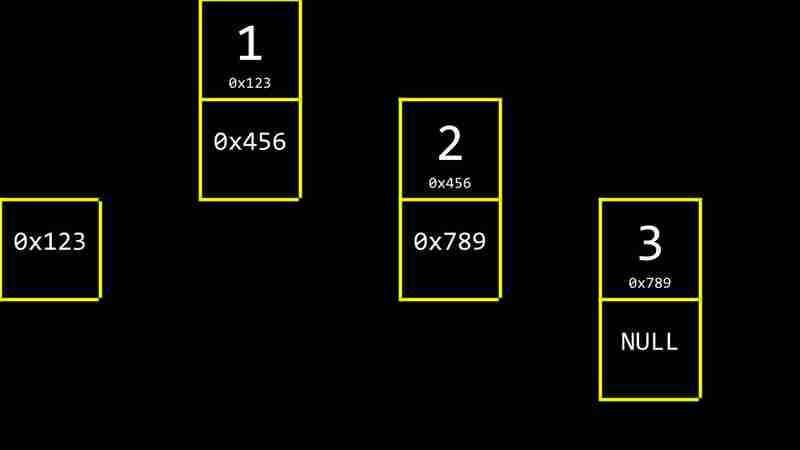
In C language, CS- Week 5s can be defined as follows:
<code class="c">typedef struct CS- Week 5 { int number; struct CS- Week 5 *next; } CS- Week 5;</code>
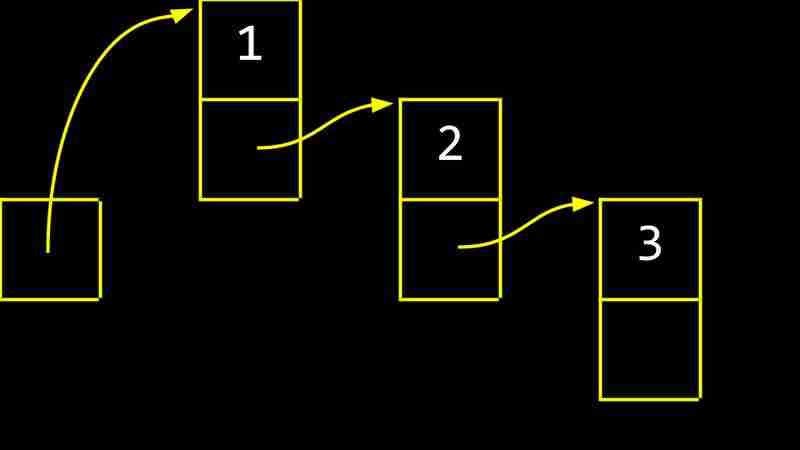
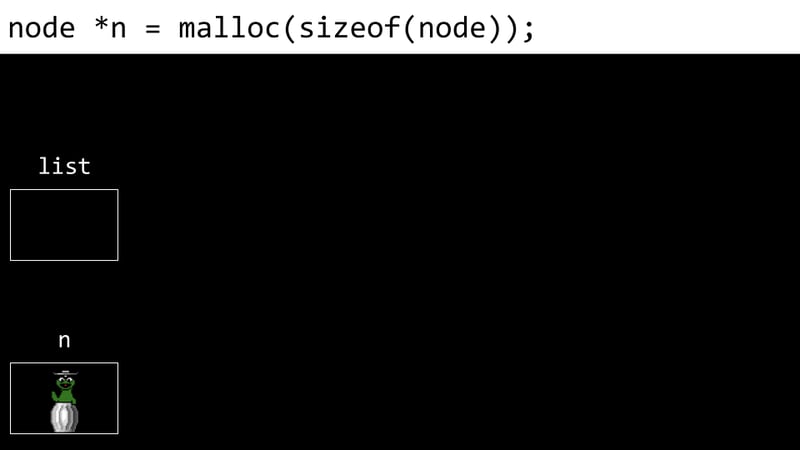
The following example shows the process of creating a linked list:

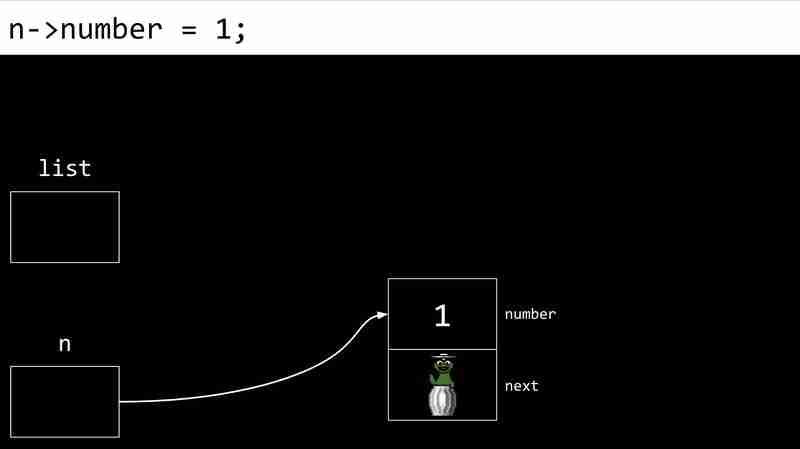
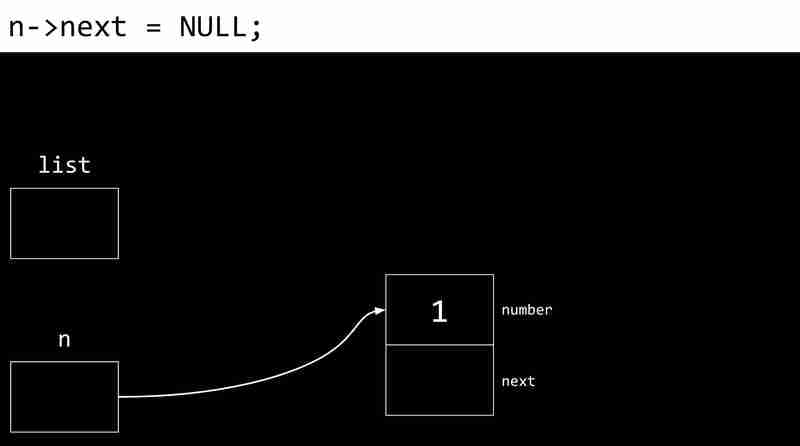
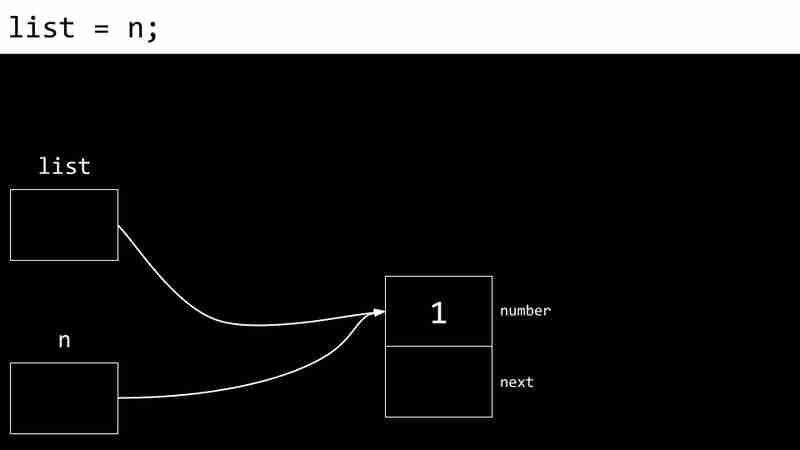
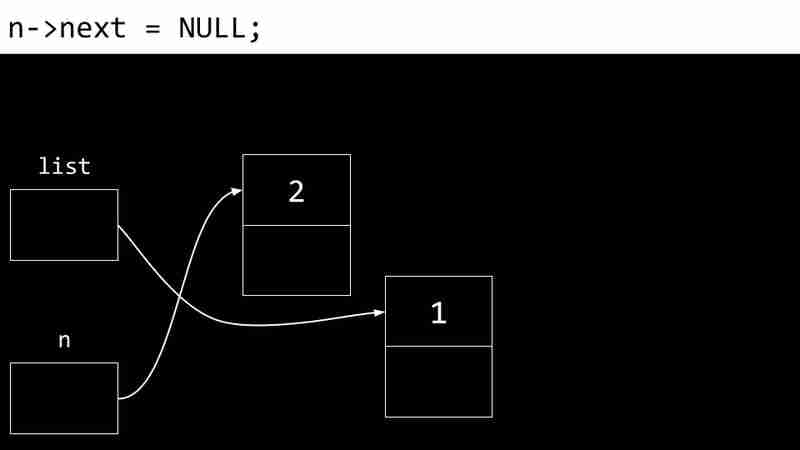
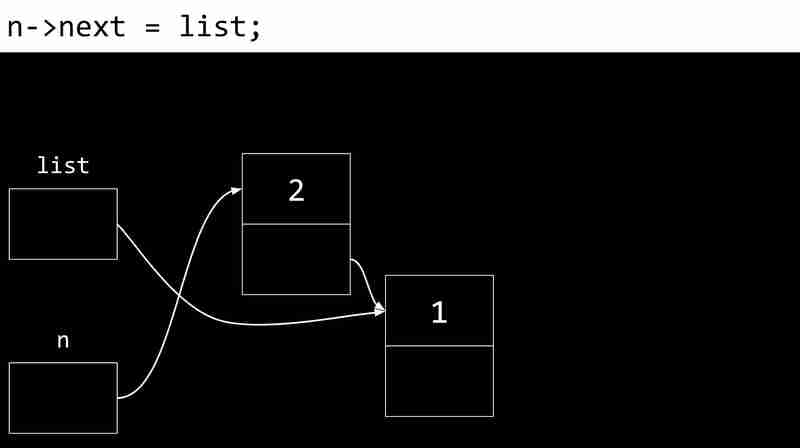

Disadvantages of linked lists include the need for additional memory storage pointers and the inability to directly access elements through indexes.
Binary Search Tree (BST)
A binary search tree is a tree structure that efficiently stores, searches and retrieves data.

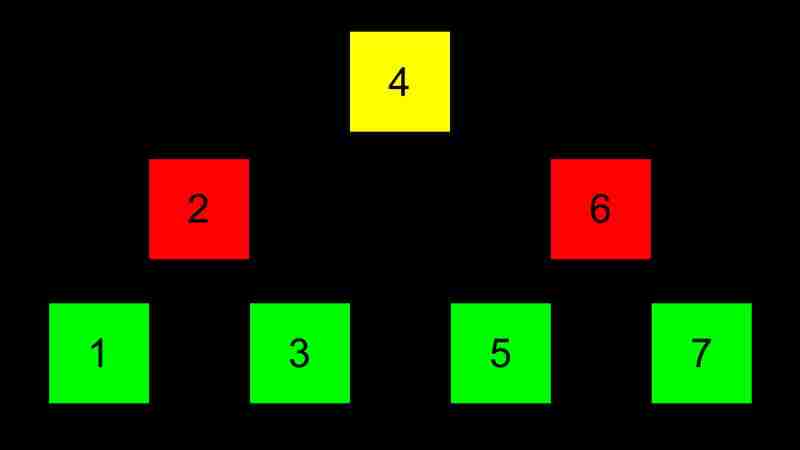
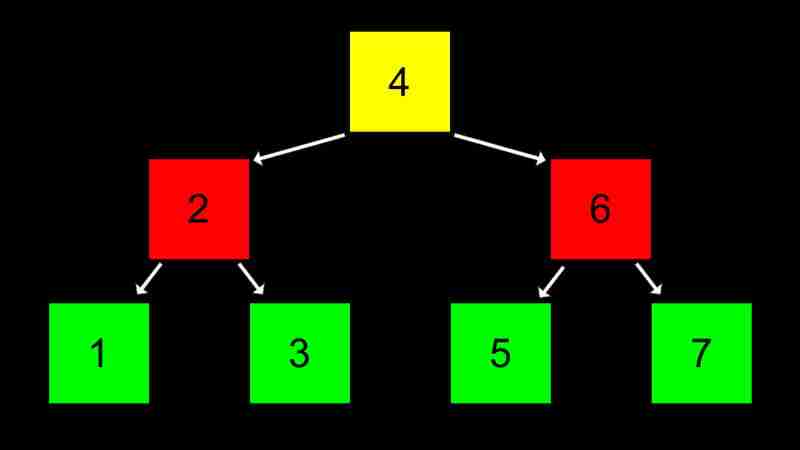
The advantages of BST are dynamic and search efficiency (O(log n)), and the disadvantage is that the search efficiency drops to O(n) when the tree is unbalanced and requires additional memory storage pointers.
Hash table
A hash table is similar to a dictionary and contains key-value pairs. It uses a hash function to map keys to array indexes, thus achieving the average lookup time of O(1).

Hash conflicts (multiple keys mapped to the same index) can be resolved by linked lists or other methods. The design of hash functions is crucial to the performance of hash tables. An example of a simple hash function is as follows:
<code class="c">#include <ctype.h> unsigned int hash(const char *word) { return toupper(word[0]) - 'A'; }</ctype.h></code>
This article is compiled based on cs50x 2024 source code.
The above is the detailed content of CS- Week 5. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How debian readdir integrates with other tools
Apr 13, 2025 am 09:42 AM
How debian readdir integrates with other tools
Apr 13, 2025 am 09:42 AM
The readdir function in the Debian system is a system call used to read directory contents and is often used in C programming. This article will explain how to integrate readdir with other tools to enhance its functionality. Method 1: Combining C language program and pipeline First, write a C program to call the readdir function and output the result: #include#include#include#includeintmain(intargc,char*argv[]){DIR*dir;structdirent*entry;if(argc!=2){
 How to implement redis counter
Apr 10, 2025 pm 10:21 PM
How to implement redis counter
Apr 10, 2025 pm 10:21 PM
Redis counter is a mechanism that uses Redis key-value pair storage to implement counting operations, including the following steps: creating counter keys, increasing counts, decreasing counts, resetting counts, and obtaining counts. The advantages of Redis counters include fast speed, high concurrency, durability and simplicity and ease of use. It can be used in scenarios such as user access counting, real-time metric tracking, game scores and rankings, and order processing counting.
 How to understand ABI compatibility in C?
Apr 28, 2025 pm 10:12 PM
How to understand ABI compatibility in C?
Apr 28, 2025 pm 10:12 PM
ABI compatibility in C refers to whether binary code generated by different compilers or versions can be compatible without recompilation. 1. Function calling conventions, 2. Name modification, 3. Virtual function table layout, 4. Structure and class layout are the main aspects involved.
 How to use the redis command
Apr 10, 2025 pm 08:45 PM
How to use the redis command
Apr 10, 2025 pm 08:45 PM
Using the Redis directive requires the following steps: Open the Redis client. Enter the command (verb key value). Provides the required parameters (varies from instruction to instruction). Press Enter to execute the command. Redis returns a response indicating the result of the operation (usually OK or -ERR).
 How to use redis lock
Apr 10, 2025 pm 08:39 PM
How to use redis lock
Apr 10, 2025 pm 08:39 PM
Using Redis to lock operations requires obtaining the lock through the SETNX command, and then using the EXPIRE command to set the expiration time. The specific steps are: (1) Use the SETNX command to try to set a key-value pair; (2) Use the EXPIRE command to set the expiration time for the lock; (3) Use the DEL command to delete the lock when the lock is no longer needed.
 How to format json in notepad
Apr 16, 2025 pm 07:48 PM
How to format json in notepad
Apr 16, 2025 pm 07:48 PM
Use the JSON Viewer plug-in in Notepad to easily format JSON files: Open a JSON file. Install and enable the JSON Viewer plug-in. Go to "Plugins" > "JSON Viewer" > "Format JSON". Customize indentation, branching, and sorting settings. Apply formatting to improve readability and understanding, thus simplifying processing and editing of JSON data.
 HadiDB: A lightweight, horizontally scalable database in Python
Apr 08, 2025 pm 06:12 PM
HadiDB: A lightweight, horizontally scalable database in Python
Apr 08, 2025 pm 06:12 PM
HadiDB: A lightweight, high-level scalable Python database HadiDB (hadidb) is a lightweight database written in Python, with a high level of scalability. Install HadiDB using pip installation: pipinstallhadidb User Management Create user: createuser() method to create a new user. The authentication() method authenticates the user's identity. fromhadidb.operationimportuseruser_obj=user("admin","admin")user_obj.
 How to deal with Redis memory fragmentation?
Apr 10, 2025 pm 02:24 PM
How to deal with Redis memory fragmentation?
Apr 10, 2025 pm 02:24 PM
Redis memory fragmentation refers to the existence of small free areas in the allocated memory that cannot be reassigned. Coping strategies include: Restart Redis: completely clear the memory, but interrupt service. Optimize data structures: Use a structure that is more suitable for Redis to reduce the number of memory allocations and releases. Adjust configuration parameters: Use the policy to eliminate the least recently used key-value pairs. Use persistence mechanism: Back up data regularly and restart Redis to clean up fragments. Monitor memory usage: Discover problems in a timely manner and take measures.






