Found a total of 10000 related content
My personal thoughts on the ThinkPHP Admin module, I don't know if it's right or not
Article Introduction:My ThinkPHP version is 3.2.3. Currently, the ways to open the backend are domain name/admin/login and domain name/admin.php/login. Then I am wondering if only one of the addresses can be specified to access the backend. I think it is this address: domain name /admin.php/login was canceled: Domain name /admin/login was checked...
2016-07-06
comment 0
994

How to Fix Magento Login Issues with Cookies and Sessions
Article Introduction:This article is a collaborative effort with Ktree. Thank you to our partners who make SitePoint possible.
This article examines how Magento cookie misconfigurations can disrupt login functionality in both the storefront and admin backend, explains t
2025-02-09
comment 0
483

Building a PhoneGap App with a WordPress Backend
Article Introduction:This tutorial demonstrates using WordPress as a backend for a PhoneGap mobile application, focusing on creating REST APIs for seamless communication. We'll build a simple login and blog post display app. While PhoneGap itself is discontinued, the p
2025-02-18
comment 0
1045

How Do I Redirect Users After Login Using JavaScript Fetch API?
Article Introduction:How to redirect the user to another page after login using JavaScript Fetch API?ProblemUsing the JavaScript code below, the authentication token is first obtained using the firebase.auth() method. A POST request is then made to the FastAPI backend. I
2024-10-18
comment 0
1215
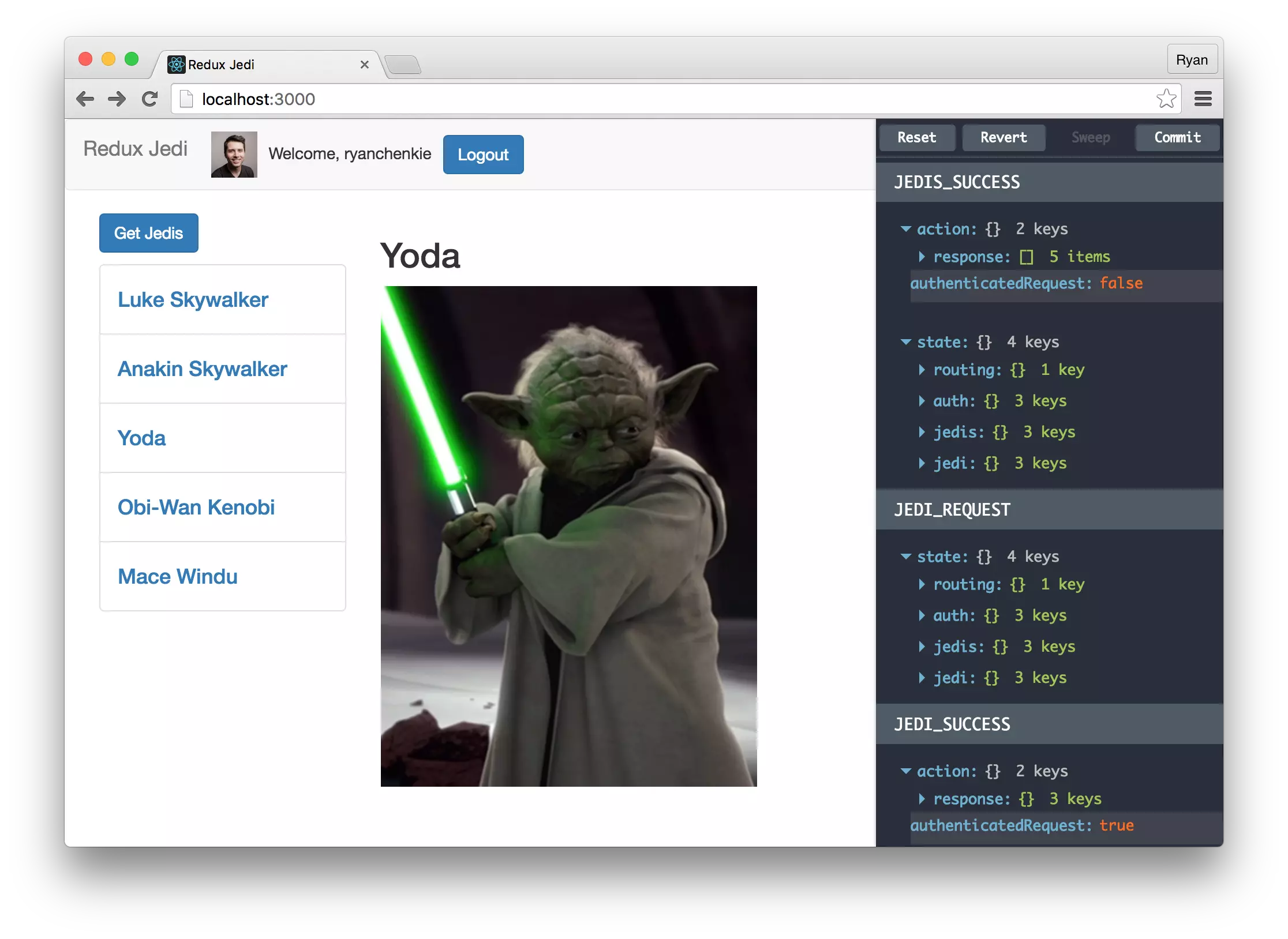
Redux Authentication: Secure Your Application with Auth0
Article Introduction:Core points
Redux provides a structured way to manage state in React applications, making data flows easy to predict and manage, especially for large applications.
Auth0 is used for user authentication, providing quick setup and advanced features such as social login and multi-factor authentication without complex backend settings.
JSON Web Tokens (JWT) is used for secure, stateless authentication against RESTful APIs, which simplifies the traditional session-based authentication process.
This tutorial simplifies the login process with Auth0's Lock widget and uses Redux middleware to handle API calls efficiently and securely.
by
2025-02-17
comment 0
711

How to implement push notifications in HTML5?
Article Introduction:Yes, HTML5 websites can implement push notifications through modern WebAPI, but they require cooperation from JavaScript, service workers and backend servers. The specific steps are as follows: 1. Check the browser support status and ensure that there is a ServiceWorker and PushManager; 2. Register a service worker to manage push events; 3. Request user authorization through Notification.requestPermission(); 4. Use the web-push library to generate a VAPID key for identity identification; 5. After the user authorization, use the pushManager.subscribe method to subscribe to the push service and send subscription information to the backend; 6. On-Service
2025-07-10
comment 0
789

Utilizing the `autocomplete` attribute in HTML5 forms.
Article Introduction:The autocomplete attribute in HTML5 helps users fill out forms faster by suggesting previously entered values, thereby improving user experience and reducing errors. It controls whether the browser automatically fills fields by setting autocomplete="on" or autocomplete="off", and some browsers may ignore the "off" setting for sensitive fields. To use this property effectively, appropriate field types and meaningful names should be combined, and specific tokens (such as autocomplete="email") can be used to improve accuracy. Common use cases include login forms, checkout pages, and registration forms;
2025-07-07
comment 0
904

What are the security best practices for a modern HTML5 application?
Article Introduction:The core security measures for developing modern HTML5 applications include: 1. Input verification and output encoding to prevent injection attacks; 2. Use HTTPS and set security response headers; 3. Control permissions and avoid excessive trust in clients; 4. Regularly check third-party dependencies. First, whitelist verification is performed on all user inputs, and secure encoding methods (such as textContent instead of innerHTML) are used when output to prevent XSS attacks; second, enable HTTPS encrypted transmission, and configure security header information such as CSP, X-Content-Type-Options, X-Frame-Options, and HSTS; third, sensitive logic needs to be verified twice on the backend, and the token should pass httpOn
2025-06-25
comment 0
402

How does the input type='email' provide client-side validation?
Article Introduction:Provide client verification and rely on the built-in browser function to check the mailbox format. 1. When using type="email", the browser automatically matches the regular expressions to ensure that the input contains @ and legal domain name formats, such as user@example.com is legal, user@ or userexample.com is illegal. 2. Verification is executed before the form is submitted, and the request is not sent to the server, but it only takes effect in modern browsers that support HTML5. 3. You can customize regular expressions in combination with pattern attributes to override default validation rules, such as limiting the length of domain name suffixes. 4. It is recommended that the backend still needs to verify the email address. Front-end verification is only an auxiliary means. At the same time, the verification lines under different browsers should be tested.
2025-06-27
comment 0
662


Dave The Diver: How To Catch Spider Crabs
Article Introduction:In Dave The Diver, there are some creatures that are not easy to catch. Or, catch alive that is. The spider crab is one of those very species, making it seem like the only way to bring these crustaceans back up to land is to viciously crack them up w
2025-01-10
comment 0
777

Prepare for Interview Like a Pro with Interview Questions CLI
Article Introduction:Prepare for Interview Like a Pro with Interview Questions CLI
What is the Interview Questions CLI?
The Interview Questions CLI is a command-line tool designed for JavaScript learners and developers who want to enhance their interview
2025-01-10
comment 0
1408

Soft Deletes in Databases: To Use or Not to Use?
Article Introduction:Soft Deletes: A Question of DesignThe topic of soft deletes, a mechanism that "flags" records as deleted instead of physically removing them, has...
2025-01-10
comment 0
1026

















