
How to Install Java 14 on CentOS/RHEL 7/8 & Fedora
Java is a secure, well-known, and stable general-purpose programming language and computing platform with numerous integrated capabilities.To run applications based on Java, you must have Java installed on your system. Typically, you will require the
Jul 08, 2025 am 09:44 AM
How to Install Skype on Rocky Linux / AlmaLinux
Skype is a widely used communication platform that allows individuals from all over the globe to connect effortlessly. With Skype, staying in touch with family, friends, and coworkers across the world becomes quick and hassle-free.The application sup
Jul 08, 2025 am 09:43 AM
How to trap signals like SIGINT or SIGTERM in Bash?
The method of using trap to capture signals is to use trap'command'SIGNAL syntax, such as trap'echo" to capture SIGINT, exiting..."'INT; the cleaning operation can be encapsulated into a function and bound multiple signals, such as trapped ingestion and binding multiple signals, such as trap's entry; precautions include avoiding calling complex commands such as exit in trap, setting trap multiple times will overwrite, resetting trap after child processes or exec, and debugging mode may affect behavior; actual applications include deleting temporary files, releasing resources, preventing errors in exit, and also ignoring signals such as trap''INT; finally, test whether the trap is effective.
Jul 08, 2025 am 01:20 AM
What are the three pillars of observability (metrics, logs, traces)?
Observability comprehensively understands the system's health through the combination of Metrics, Logs and Traces. 1.Metrics provides quantitative data snapshots, such as CPU usage, which is suitable for real-time monitoring but cannot locate specific problems; 2.Logs records detailed event information, which is suitable for troubleshooting specific errors but large data volume; 3.Traces tracks request links and locates performance bottlenecks, requiring unique identification and context delivery. They ensure system transparency from three levels: overall state, specific details and process path.
Jul 08, 2025 am 01:11 AM
What is the role of each component in the ELK Stack?
TheELKStackisasuiteoftoolsforreal-timelogdatahandling,composedofElasticsearch,Logstash,Kibana,andBeats.1.Elasticsearchstoresandsearchesstructuredorunstructureddataefficiently,idealfortime-serieslogs.2.Logstashcollects,parses,andtransformsrawdatafromv
Jul 08, 2025 am 12:58 AM
What is the best Linux distro for beginners?
For newbies who are just starting to get involved in Linux, the best choice is Ubuntu. It is the most recommended distribution for beginners, with a user-friendly interface, huge community support, and a desktop environment similar to Windows or macOS. Ubuntu provides a stable system, detailed documentation and simple graphical installer, and uses a widely used APT package manager to facilitate learning of other Debian-based distributions. It also offers a long-term support (LTS) version with a support cycle of up to five years and software installation can be done via the Ubuntu Software Center or the command line. In addition, there are a large number of tutorials, forums and guides online to facilitate problem solving. It is recommended that novices choose the LTS version for a more stable experience. Other choices for beginners
Jul 08, 2025 am 12:48 AM
What are zombie and orphan processes?
The Zombie process is a process that has been executed but has not been recycled by the parent process because the parent process does not call wait() to read its state; it does not occupy resources but will occupy process table entries. The Orphan process is that the parent process terminates before the child process, and the child process is taken over by init/systemd; it can run normally until it ends. Both are not dangerous, but it should be noted: too many zombie processes will exhaust the process table and the parent process code needs to be repaired; if the orphan process is out of control, it may waste resources, and monitoring should ensure that it ends correctly.
Jul 08, 2025 am 12:38 AM
What are standard input, standard output, and standard error in Linux?
In Linux, standard input (stdin), standard output (stdout), and standard error (stderr) are the three streams available by default for each process. 1.stdin (file descriptor 0) is used for the program to read input, and the default is from the keyboard; 2.stdout (file descriptor 1) is used for the program to output normal results, and the default is displayed in the terminal; 3.stderr (file descriptor 2) is used for the program to output error information, and the default is also displayed in the terminal. The source or destination of these streams can be changed through the redirect operator, for example > redirect stdout to a file, 2 > redirect stderr alone, > with >> control overwrite or append content, /dev/null can
Jul 08, 2025 am 12:31 AM
How to find and manage files in Linux?
Find files in Linux system can be found and locate. Real-time search for find is suitable for filtering by condition. Locate depends on database updates quickly; 2. Use ls, tree or graphical interface to browse the directory structure, and tree displays the tree structure more intuitively; 3. File management uses CP, mv, and rm commands to copy, move and delete, note that rm deletion is irreversible; 4. Use ls-lt to sort files by time and ls-a to view hidden files. By mastering these commonly used commands and ideas, Linux file operations will become efficient and convenient.
Jul 08, 2025 am 12:28 AM
How to list files in a Linux terminal
The most common way to view file lists in Linux terminals is to use the ls command; 1. Basic usage: Enter ls directly to list the current directory contents, sort by name by default and ignore hidden files; 2. View detailed information: Use ls-l to display attributes such as permissions, size, time, etc.; 3. Show hidden files: Use ls-a or ls-la to view hidden files; 4. Distinguish files by type: ls-F will add symbol marks after the file, such as / represents a directory, * represents an executable file; 5. Color highlighting: ls--color displays file types in different colors to improve visualization effect.
Jul 08, 2025 am 12:21 AM
How to parse JSON from a shell script using jq?
ToparseJSONinshellscriptsusingjq,youcanutilizeitsfilteringsyntaxtoextractvaluesfromstructureddata.StartbypipingJSONinputintojqorspecifyingafile,suchasecho'{"name":"Alice"}'|jq'.name'orjq'.name'data.json,whichextractsthevalueofthe&
Jul 08, 2025 am 12:13 AM
How to configure logrotate for custom log files?
TosetuplogrotateforcustomlogfilesonaLinuxserver,createaconfigurationfilein/etc/logrotate.d/,definerotationrules,testthesetup,andhandleappsthatdon’treopenlogs.1.Createaconfigfilelike/etc/logrotate.d/myappwithrulessuchasdaily,rotate,compress,delaycompr
Jul 08, 2025 am 12:01 AM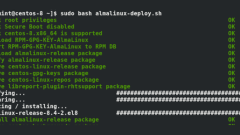
How to Migrate from CentOS 8 to AlmaLinux 8.5
In our previous guide, we guided you through the installation of AlmaLinux. If you currently have CentOS 8 running, there's an automated migration script available that allows you to smoothly transition to the latest version of AlmaLinux 8.5 without
Jul 07, 2025 am 09:25 AM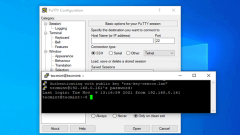
How to Setup Passwordless Linux Login Using Putty on Windows
SSH (Secure SHELL) is among the most popular network protocols for connecting and logging into remote Linux servers. Its popularity comes from the enhanced security it offers through a cryptographic secure channel that protects data flow over insecur
Jul 07, 2025 am 09:24 AM
Hot tools Tags

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

vc9-vc14 (32+64 bit) runtime library collection (link below)
Download the collection of runtime libraries required for phpStudy installation

VC9 32-bit
VC9 32-bit phpstudy integrated installation environment runtime library

PHP programmer toolbox full version
Programmer Toolbox v1.0 PHP Integrated Environment

VC11 32-bit
VC11 32-bit phpstudy integrated installation environment runtime library

SublimeText3 Chinese version
Chinese version, very easy to use








